How to Create an Image of Your PC Before Upgrading to Windows 10
Windows 10 is the biggest and most aggressive Windows rollout to date. Before you take the plunge you need to image your hard drive so, should you wish to return to the familiarity of Windows 7 or Windows 8 you can do so with the click of a button.
Note: This tutorial details how to create a bit-for-bit backup (a disk image) of your current Windows system disk so that you can later restore your computer using that image. If that’s not what you’re looking for and you’d like to actually copy your disk bit-for-bit over to a brand new hard disk (a disk clone) we’d encourage you to check out our detailed tutorial on the matter:How to Upgrade Your Existing Hard Drive in Under an Hour.
Why Do I Want To Do This?
There’s nothing worse than making a major change to your PC and then finding out that change breaks your workflow (like an old app you rely on doesn’t work anymore) or it outright breaks your PC because the leap to a new operating system leaves your hardware in need of new (and as-of-yet unreleased) drivers.
Over the years we’ve covered plenty of ways to use the tools built into Windows to perform snapshots, create backups, and otherwise help you to restore your computer to a prior state if your hardware upgrades or such go awry. When it comes to a change as big as jumping from Windows 7 or Windows 8 to the barely charted waters of Windows 10, however, you don’t want to rely on snapshots and rollback features to help you return to the safety of a prior version of Windows. You want the clear and precise ability to wipe the entire drive clean and restore it, bit for bit, to the exact state it was in before you even started the upgrade process.
In order to do that we need to image the drive. We want a perfect pre-upgrade copy we can call upon to restore the system. This drive image will remain clean and unchanged independently of anything we do to the computer during the upgrade process and thereafter so even if we format the drives, even if we use Windows 10 for six months and decide we really don’t like it, we can turn right back around and use the image we’ve created to turn back the clock and restore our computer to the exact state it was in before the upgrade.
We can’t emphasize enough how important this step is. We’ll complete it using free tools, it doesn’t cost anything (unless you need to purchase an extra drive to store the image on), and it hardly takes any time (especially when you compare it to the hassle of reinstalling your old version of Windows and reconfiguring everything).
What Do I Need?
As we highlighted in the introduction this procedure is free (unless you need an additional internal or external hard drive to house the drive image). To follow along with us today you’ll need the following things:
- The PC you wish to backup.
- A copy of Macrium Reflect Free (available for download here).
- An internal or external hard drive with enough capacity to hold the contents of the drive you wish to image.
- A USB drive to turn into a restoration drive (minimum size 1GB).
A few points of consideration before we proceed. We aren’t cloning your Windows drive onto a new bootable drive so we don’t need a fresh storage drive or a drive we can wipe. As long as you have the space you can use any drive you have on hand as long as it can hold the drive image. So, for example, if you have a 2TB external drive that you have a few hundred GB of photos backed up on, you can also use it (space permitting) to backup your Windows disk image with no risk to your photos or other data.
Although we advise you to have enough space for the whole drive, in reality the disk likely isn’t full and compression will buy you some wiggle room. On our test laptop, for example, we had a 100GB SSD, 75GB of that was filled up, and the compressed image in the end was only 50GB. Still, act as if you need a 1:1 space ratio and then be happy when you don’t.
Before proceeding gather together the required materials and take a moment to download and install Macrium Reflect Free.
Creating the Rescue Media
Because we are manipulating the system drive we need rescue media in order to properly restore the drive later (as we cannot simultaneously use the system drive and reload the system image). Further, good rescue media can be invaluable for troubleshooting problems down the road.
Thankfully Macrium makes it incredibly simple to create a Windows PE-based rescue media tool that includes Macrium preloaded and even boots right into the restoration tool. It couldn’t be easier and if you do things correctly on the setup and imaging side of things, the restoration side of things is a walk in the park.
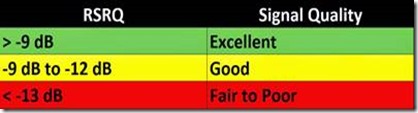
Once you’re ready to create your restoration media, launch Macrium Reflect on select Other Tasks -> Create Rescue Media from the file bar, as seen above.
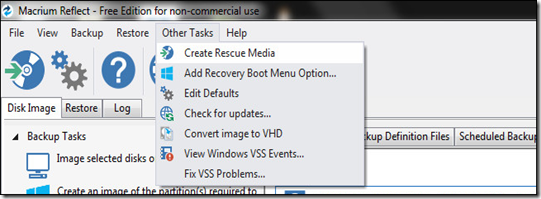
The Rescue Wizard is very helpful and will not only guide you through selecting the best rescue media but will automatically download and install the files from Microsoft on your behalf. The first step in the wizard process is confirming you have the right version of Windows PE. It automatically detects the version of Windows you’re creating the rescue media on. Ideally you want the rescue media to use the version of Windows PE that shares the same base kernel as the backup version.
If you’re backing up a Windows 7 machine before upgrading to Windows 10 that means you want Windows PE 3.1 (which uses the Windows 7 kernel). If you’re upgrading from Windows 8/8.1 to Windows 10 you want Windows PE 5.0 (PE 4.0 is an option but it’s not feature rich compared to PE 5.0 and the special use case for Windows PE 4.0 is very limited and definitely not within the requirements of anything we’re doing in this tutorial). If you need to change your PE version click on the button labeled “Change PE Version” at the bottom of the wizard screen.
Click Next and then confirm the drivers list (by default the media thoughtfully snags needed drivers from the host Windows installation, like USB 3.0 host drivers). Click Next.
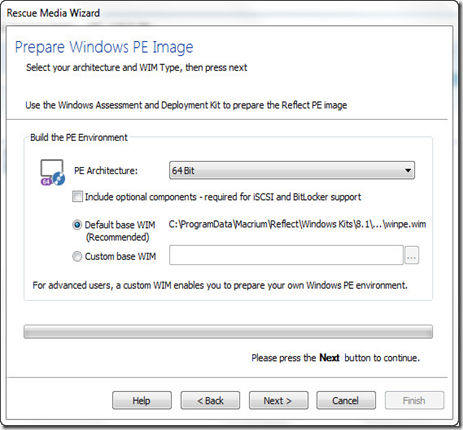
Confirm that the “PE Architecture” matches your machine (it should have defaulted to the correct setting). Newer machines (made recently or in the last few years) are almost universally 64 bit. If you’re unsure you can read up on the differences between 64 bit and 32 bit (and how to check what you have) in our article HTG Explains: What’s the Difference Between 32-bit and 64-bit Windows?
Click Next and you’ll be prompted to OK a download from Microsoft (typically around 500MB).
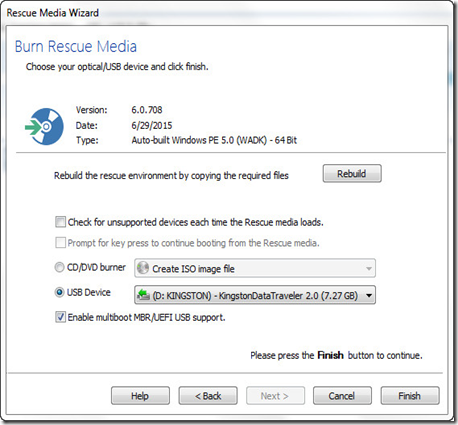
Once the files from Microsoft finish downloading you’ll find yourself in the final step of the Rescue Media Wizard. Select your USB drive carefully; while the recovering media creation process doesn’t format your USB drive it does dump a bunch of files onto the disk and make some minor modifications you’ll just have to turn around and undo.
When the process is complete it’s safe to eject the recovery disk (you won’t need it again until it is time to restore your system at a later date).
Cloning Your Windows Disk
This portion of the tutorial occurs on your PC before installing Windows 10. Again, for emphasis as many readers following this tutorial likely don’t routinely use disk imaging software, this step occurs on your machine before you begin the Windows 10 upgrade.
Now would be a great time to do some last minute housekeeping: delete things you don’t need, run CCleaner to purge old temporary files that don’t need to live on forever in your disk image, uninstall apps you no longer want or need, and so on.
When you’re ready to create a perfect copy of the disk in a tidy pre-Windows 10 state, launch Macrium Reflect. In the left-hand navigation panel of the main window select “Create an image of the partition(s) required to backup and restore Windows” as seen in the screenshot below.

That link will automatically pop up Disk Image dialogue box with only the critical Windows partitions selected, as seen in the screenshot below.
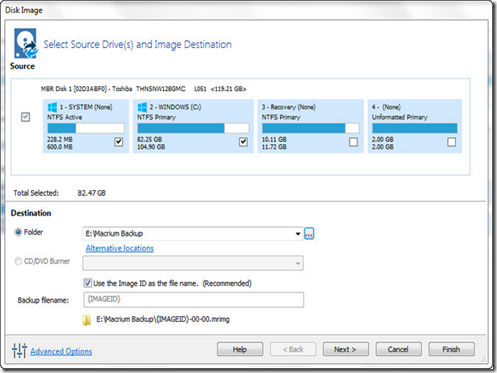
There are a few important things to note here. By default the tool only selects the partitions you need to actually run Windows. In the screenshot above you can see that it selected the system and OS partitions. It did not select the recovery partition or other partitions on the primary disk. If you wish to preserve the recovery partition or other partitions, you can check them and include them in the disk image. If you don’t (we really don’t care if the recovery partition is preserved) leave them unchecked. If you do, check them off.
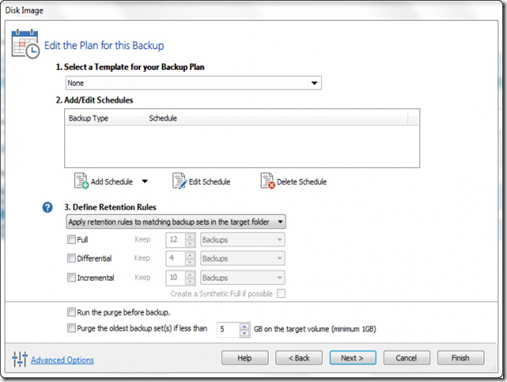
Next, select where you wish to store the image file. A local non-OS disk or a removable USB drive of suitable size is good. We stored ours on a removable USB 3.0 drive with plenty of space to spare. Click Next and you’ll be prompted to setup a backup plan for the disk. You can ignore all of these options. Macrium Reflect, even in the free version, has a very excellent automated backup system but that’s totally overkill for our needs as we’re making a one off backup. Leave the template “None”, don’t bother setting a schedule, and leave everything unchecked. Hit Next to continue on.
Confirm your settings on the last page (make sure the listed operations match what you selected earlier, like copying the system and Windows disks). Click Finish. In the final screen confirm “Run this backup now” is checked and click OK.
Sit back and relax as Macrium works to create the disk image. Expect to wait at least 30-60 minutes at minimum. When the process is complete you’ll have a perfect copy of your disk ready to pull out and restore the previous version of Windows. Put it in a safe place!
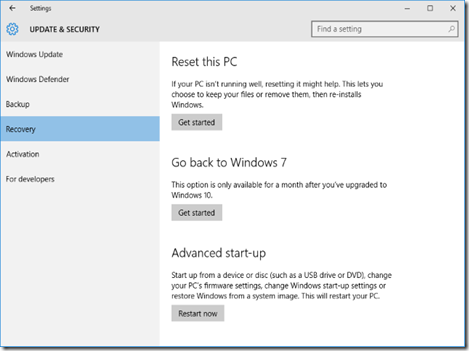
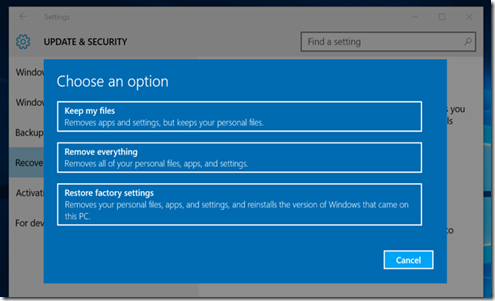
How Do I Restore To The Old Version?
Maybe you love Windows 10 and everything works wonderfully. We certainly never hope that someone is unhappy with an upgrade and despite all the complaints about Windows 8 we (albeit with a Windows 7 skin on things) were happy with the improvements. But not every upgrade is a match made in heaven and you might find that instabilities, non-existent drivers, or other problems hamper your enjoyment of Windows 10.
In such cases you’ll need to rollback with the help of Macrium Reflect and the disk image we just created. First things first, to avoid frustration, reboot your computer and enter the BIOS (it varies from manufacturer to manufacturer, but typically you access the BIOS via F2 or F11 on the keyboard when the computer is first booting).
It’s not enough to have a computer that can boot from USB, you need to check the boot order. More times than we can count we’ve had a boot disk fail because while the computer was more than capable of booting from a USB drive the USB drive option was third in the list after the physical hard disk and CDROM drive. Double check that the USB drive is at the top of the list! (Sometimes you actually need the physical USB drive inserted during the BIOS adjustment process or it won’t be detected or ordered properly). Save the changes and boot into your recovery media.
The recovery media we created in the early portion of the tutorial automatically boots right to the Macrium Reflect recovery software which is more than convenient. Once it boots up look for the Restore and Image Restore tabs as seen in the screenshot below.
If you’ve booted the computer with the hard drive that houses the disk image attached (either internally mounted or with the USB drive attached to the computer) it should automatically detect that the disk image is present and it matches the disk you’re about the restore via that image. If it doesn’t automatically detect don’t worry, you can browse for it.
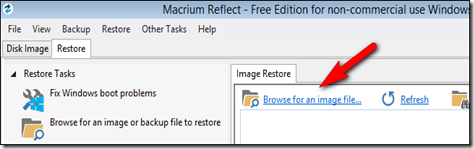
Click on the entry “Browse for an image file”. Browse for the file and select the .MRIMG file you previously created. After you load the backup image you’ll see additional information about the image file.

Confirm that it is the correct image file (the name matches the one you want, the drive size and partitions match, and so on). Once you’ve confirmed it is the image you want, click the link “Restore Image” as seen in the screenshot above.

You’ll be prompted to select a disk to restore your image to. Click “Select a disk to restore to…”
Select carefully from the available disks. You don’t want to overwrite your secondary data hard drive when your real target is your primary system disk. Once you’ve selected the image, then click “Copy selected partitions” to copy the partitions from the image file back over to your disk.
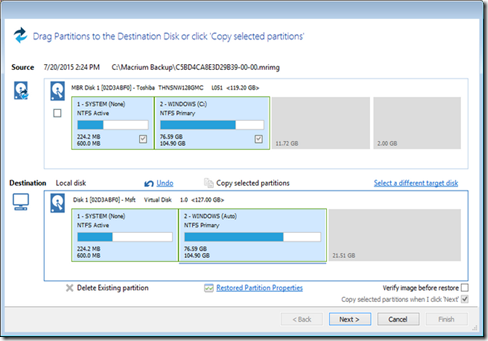
Note: Sharp-eyed readers will likely have noticed that the disk size and partition distribution between our source disk and our destination disk do not match up in the above image. Because the computer with which we conducted the steps for this tutorial (as we personally test and confirm all steps in all articles we write here at How-To Geek) would not cooperate with our capture tool during the time it was booted into Windows PE we recreated the sequence in a virtual machine expressly to create the screenshots for your reference. Please note that in the particular application we’ve using here (overwriting your existing disk with an old image) the image and the actual hard drive configuration should match up.
With the disk selected (and double checked), click Next. Confirm the Restore Summary and Operation list match what you expect and then click Finish to start the process.
When the restoration process is complete and the conclusion summary is displayed, you’re all done! Click on the shutdown button located in the lower left corner of the restoration user interface, remove the USB restoration drive, and confirm you wish to restart. You’ll boot back into your Windows machine and everything will be good as new and exactly like it was the day you made the image.
When it comes to foolproof restoration you just can’t beat a good disk image. Before you make the leap to Windows 10 take an hour or so and make a clean disk image you can return to should you find the upgrade isn’t all it’s promised to be.
Taken From: http://www.howtogeek.com/223139/how-to-create-an-image-of-your-pc-before-upgrading-to-windows-10/