By default BGP will advertise all prefixes to EBGP (External BGP) neighbors. This means that if you are multi-homed (connected to two or more ISPs) that you might become a transit AS. Let me show you an example:
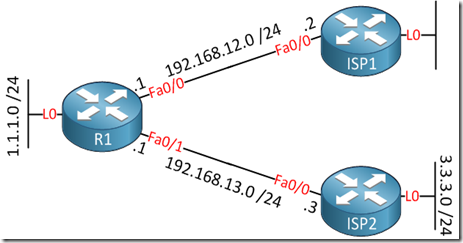
R1 is connected to ISP1 and ISP2 and each router is in a different AS (Autonomous System). Since R1 is multi-homed it’s possible that the ISPs will use R1 to reach each other. In order to prevent this we’ll have to ensure that R1 only advertises prefixes from its own autonomous system.
As far as I know there are 4 methods how you can prevent becoming a transit AS:
- Filter-list with AS PATH access-list.
- No-Export Community.
- Prefix-list Filtering
- Distribute-list Filtering
Prefix-lists or distribute-lists will work but it’s not a very scalable solution if you have thousands of prefixes in your BGP table. The filter-list and no-export community work very well since you only have to configure them once and it will not matter if new prefixes show up. First we’ll configure BGP on each router:
R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.12.2 remote-as 2
R1(config-router)#neighbor 192.168.13.3 remote-as 3
ISP1(config)#router bgp 2
ISP1(config-router)#neighbor 192.168.12.1 remote-as 1
ISP2(config)#router bgp 3
ISP2(config-router)#neighbor 192.168.13.1 remote-as 1
The commands above will configure EBGP (External BGP) between R1 – ISP1 and R1 – ISP2. To make sure we have something to look at, I’ll advertise the loopback interfaces in BGP on each router:
R1(config)#router bgp 1
R1(config-router)#network 1.1.1.0 mask 255.255.255.0
ISP1(config)#router bgp 2
ISP1(config-router)#network 2.2.2.0 mask 255.255.255.0
ISP2(config)#router bgp 3
ISP2(config-router)#network 3.3.3.0 mask 255.255.255.0
With the networks advertised, let’s take a look at the BGP table of ISP1 and ISP2 to see what they have learned:
ISP1#show ip bgp
BGP table version is 4, local router ID is 11.11.11.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.12.1 0 0 1 i
*> 2.2.2.0/24 0.0.0.0 0 32768 i
*> 3.3.3.0/24 192.168.12.1 0 1 3 i
ISP2#show ip bgp
BGP table version is 4, local router ID is 33.33.33.33
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.13.1 0 0 1 i
*> 2.2.2.0/24 192.168.13.1 0 1 2 i
*> 3.3.3.0/24 0.0.0.0 0 32768 i
The ISP routers have learned about each other networks and they will use R1 as the next hop. We now have everything in place to play with the different filtering techniques.
Filter-list with AS PATH access-list
Using an filter-list with the AS PATH access-list is probably the most convenient solution. It will ensure that you will always only advertise prefixes from your own autonomous system.
Here’s how to do it:
R1(config)#ip as-path access-list 1 permit ^$
R1(config-router)#neighbor 192.168.12.2 filter-list 1 out
R1(config-router)#neighbor 192.168.13.3 filter-list 1 out
The ^$ regular expression ensures that we will only advertise locally originated prefixes. We’ll have to apply this filter to both ISPs.
Keep in mind that BGP is slow…if you are doing labs, it’s best to speed things up with clear ip bgp *
Let’s verify our configuration:
R1#show ip bgp
BGP table version is 4, local router ID is 22.22.22.22
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 0.0.0.0 0 32768 i
*> 2.2.2.0/24 192.168.12.2 0 0 2 i
*> 3.3.3.0/24 192.168.13.3 0 0 3 i
R1 still knows about the prefixes from the ISP routers. What about ISP1 and ISP2?
ISP1#show ip bgp
BGP table version is 7, local router ID is 11.11.11.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.12.1 0 0 1 i
*> 2.2.2.0/24 0.0.0.0 0 32768 i
ISP2#show ip bgp
BGP table version is 7, local router ID is 33.33.33.33
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.13.1 0 0 1 i
*> 3.3.3.0/24 0.0.0.0 0 32768 i
ISP1 and ISP2 only know about the 1.1.1.0 /24 network. Excellent, we are no longer a transit AS! On to the next method…
No-Export Community
Using the no-export community will also work pretty well. We will configure R1 so that prefixes from the ISP routers will be tagged with the no-export community. This ensures that the prefixes from those routers will be known within AS 1 but won’t be advertised to other routers.
R1(config)#route-map NO-EXPORT
R1(config-route-map)#set community no-export
R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.12.2 route-map NO-EXPORT in
R1(config-router)#neighbor 192.168.13.3 route-map NO-EXPORT in
I’m only using one router in AS 1, if you have other routers and are running IBGP (Internal BGP) then don’t forget to send communities to those routers with the neighbor <ip> send-community command.
Let’s see what ISP1 and ISP2 think about our configuration:
ISP1#show ip bgp
BGP table version is 11, local router ID is 11.11.11.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.12.1 0 0 1 i
*> 2.2.2.0/24 0.0.0.0 0 32768 i
ISP2#show ip bgp
BGP table version is 11, local router ID is 33.33.33.33
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.13.1 0 0 1 i
*> 3.3.3.0/24 0.0.0.0 0 32768 i
They only know about network 1.1.1.0 /24. Onto the next method!
Prefix-List Filtering
Using a prefix-list we can determine what prefixes are advertised to our BGP neighbors. This works fine but it’s not a good solution to prevent becoming a transit AS. Each time you add new prefixes you’ll have to reconfigure the prefix-list. Anyway let me show you how it works:
R1(config)#ip prefix-list NO-TRANSIT permit 1.1.1.0/24
R1(config-router)#neighbor 192.168.12.2 prefix-list NO-TRANSIT out
R1(config-router)#neighbor 192.168.13.3 prefix-list NO-TRANSIT out
The prefix-list above will only advertise 1.1.1.0 /24 to the ISP routers. Let’s verify the configuration:
ISP1#show ip bgp
BGP table version is 17, local router ID is 11.11.11.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.12.1 0 0 1 i
*> 2.2.2.0/24 0.0.0.0 0 32768 i
ISP2#show ip bgp
BGP table version is 17, local router ID is 33.33.33.33
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.13.1 0 0 1 i
*> 3.3.3.0/24 0.0.0.0 0 32768 i
The prefix-list is working as it should, onto the last exercise!
Distribute-list Filtering
This method is similar to using the prefix-list but this time we’ll use an access-list.
R1(config)#ip access-list standard NO-TRANSIT
R1(config-std-nacl)#permit 1.1.1.0 0.0.0.255
R1(config-router)#neighbor 192.168.12.2 distribute-list NO-TRANSIT out
R1(config-router)#neighbor 192.168.13.3 distribute-list NO-TRANSIT out
Time to check the ISPs:
ISP1#show ip bgp
BGP table version is 23, local router ID is 11.11.11.11
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.12.1 0 0 1 i
*> 2.2.2.0/24 0.0.0.0 0 32768 i
ISP2#show ip bgp
BGP table version is 23, local router ID is 33.33.33.33
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale
Origin codes: i - IGP, e - EGP, ? - incomplete
Network Next Hop Metric LocPrf Weight Path
*> 1.1.1.0/24 192.168.13.1 0 0 1 i
*> 3.3.3.0/24 0.0.0.0 0 32768 i
That’s all there is to it. I hope this has been helpful for you, if you know of any other methods to prevent becoming a BGP transit AS please leave a comment!
Taken From: http://networklessons.com/bgp/bgp-prevent-transit-as/


![clip_image001[1] clip_image001[1]](http://lh3.ggpht.com/-Y49TJvqJGWE/Ui5NKEpoaGI/AAAAAAAACgg/2Mzbmz6hNuY/clip_image001%25255B1%25255D_thumb.jpg?imgmax=800)